In a digital era where cyber threats are becoming increasingly complex and evasive, traditional malware detection methods often fall short. Enter hybrid analysis, a sophisticated approach that combines the best of both static and dynamic analysis techniques to detect, dissect, and defend against modern cyberattacks. Hybrid analysis bridges the gap between code inspection and behavioral observation, offering unparalleled depth and precision in identifying malicious software.
As attackers evolve their techniques, from code obfuscation to sandbox evasion, security professionals need a toolset that can adapt just as quickly. Hybrid analysis is emerging as a critical method in cybersecurity, offering the ability to not only detect known threats but also analyze new, unseen malware strains. It’s particularly useful in today’s environment of zero-day vulnerabilities and advanced persistent threats (APTs).
This article offers a comprehensive breakdown of hybrid analysis: what it is, how it works, the tools involved, real-world applications, and the future trends shaping its evolution. Whether you’re a cybersecurity professional, a malware analyst, or simply curious about how digital threats are tackled, this guide will equip you with a deep understanding of one of the most powerful tools in modern cyber defense.
Understanding Hybrid Analysis Concept and Evolution
Hybrid analysis is a technique that fuses static and dynamic analysis to provide a well-rounded assessment of a file or application. While static analysis involves inspecting the code structure without executing it, dynamic analysis focuses on observing the file’s behavior during execution in a controlled environment. The hybrid approach allows analysts to enjoy the benefits of both: the thoroughness of code-level inspection and the contextual insights from real-time behavior tracking.
Traditional malware analysis relied heavily on static techniques like signature matching and heuristic checks. However, as malware authors began using encryption and polymorphism to disguise code, static analysis became less effective on its own. Conversely, dynamic analysis can reveal how malware interacts with system resources but can miss subtle clues hidden in the codebase or be thwarted by anti-analysis techniques.
The hybrid method evolved as a response to these limitations. By combining both approaches, it provides a layered defense mechanism that can uncover hidden malicious intent and deliver actionable intelligence. In essence, it doesn’t just tell you what a file does, but also how and why it behaves the way it does. This comprehensive view has made hybrid analysis indispensable in the fight against sophisticated malware threats.
Core Components of Hybrid Analysis
At its heart, hybrid analysis consists of two primary components: static analysis and dynamic analysis. Static analysis is the process of examining the source code, binaries, or metadata of a file without running it. It helps identify strings, function calls, IP addresses, encryption methods, and other embedded information that may hint at malicious intent. It is fast, safe, and useful for known threats but may be less effective against encrypted or obfuscated malware.
Dynamic analysis, on the other hand, executes the file within a sandbox or virtual environment. It watches how the file behaves — does it create suspicious processes, modify registry keys, or attempt to connect to remote servers? Dynamic analysis excels at catching runtime behavior, especially when malware only activates under certain conditions.
The strength of hybrid analysis lies in the integration of these methods. For example, if static analysis finds suspicious encryption routines and dynamic analysis confirms the program communicates with a blacklisted IP, the system can correlate these findings to reach a higher-confidence verdict. Additionally, machine learning algorithms can further enhance this integration by learning from previous analyses and improving future detection accuracy.
Automation also plays a critical role. Modern hybrid analysis tools often integrate with security information and event management (SIEM) systems, streamlining the threat detection pipeline from alert generation to response. This synergy reduces investigation time and boosts the efficacy of incident response teams.
Tools and Platforms for Hybrid Analysis
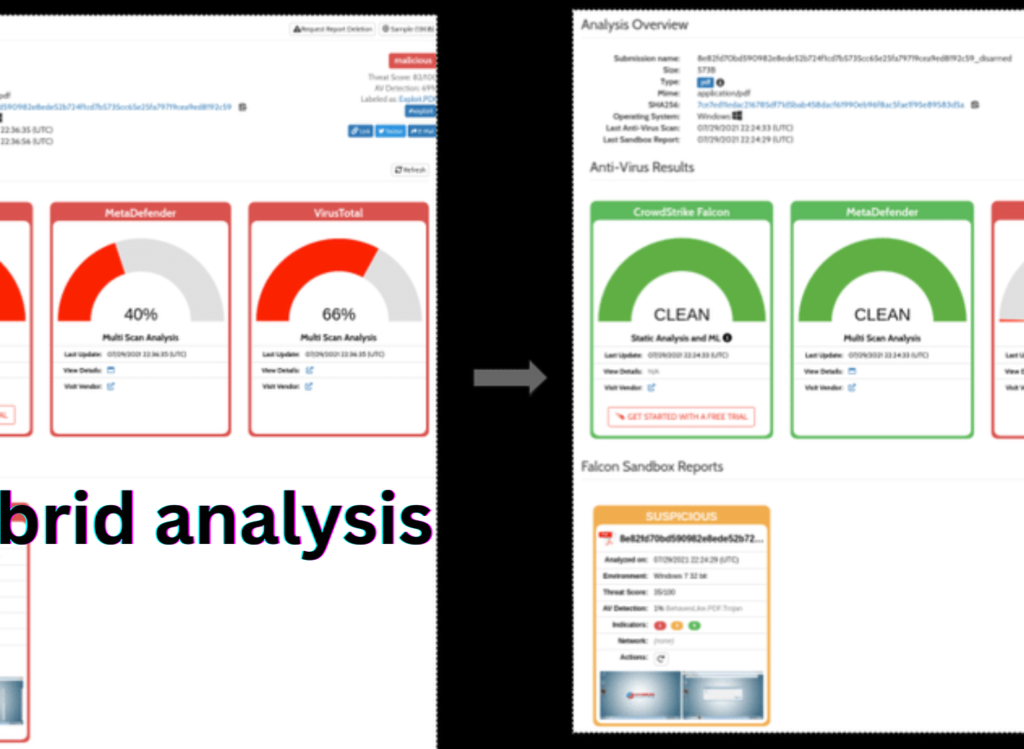
Several powerful tools and platforms support hybrid analysis, ranging from open-source solutions to enterprise-grade platforms. One of the most well-known tools is Hybrid Analysis by CrowdStrike, formerly developed by Payload Security. It offers a cloud-based sandbox environment that automatically analyzes files using both static and dynamic techniques. Its intuitive interface, detailed reports, and community-driven threat intelligence make it a go-to solution for many cybersecurity professionals.
Cuckoo Sandbox is another widely-used open-source tool that allows users to perform dynamic analysis in a customizable environment. Although it requires technical expertise to set up and operate, its flexibility and extensibility make it a favorite among researchers. When paired with static analysis tools like Binwalk, Ghidra, or IDA Pro, Cuckoo becomes part of a hybrid analysis workflow.
Joe Sandbox is a commercial product that supports a wide range of file types and environments, including Windows, Android, macOS, and Linux. It offers deep behavior analysis, real-time screenshots, and advanced evasion detection, making it ideal for enterprise environments.
Choosing the right tool depends on several factors: budget, desired level of automation, platform support, and integration capabilities with existing infrastructure. While open-source tools offer flexibility, commercial platforms often come with support, regular updates, and easier deployment — crucial for organizations with limited internal cybersecurity expertise.
Use Cases and Applications in Cybersecurity
Hybrid analysis is not just a theoretical concept — it is actively reshaping how cybersecurity teams approach threat detection and response. One of the most critical applications is in enterprise security operations. Organizations use hybrid analysis to scan incoming emails, attachments, and downloaded files for embedded malware. With the increase in phishing and ransomware attacks, hybrid analysis serves as a frontline defense by catching threats that evade signature-based detection.
In incident response and digital forensics, hybrid analysis helps teams quickly determine the impact of a breach. By analyzing the payload and behavior of the malicious file, responders can map out the attack vector, affected systems, and potential data exfiltration — all of which are vital for containment and recovery.
Antivirus and EDR vendors integrate hybrid analysis into their engines to improve threat detection rates. Instead of relying solely on known malware signatures, hybrid analysis enables proactive defense against polymorphic and zero-day malware. It also feeds threat intelligence platforms, enriching them with behavioral indicators and file hashes for future reference.
Government and military agencies also leverage hybrid analysis in their cyber defense operations. These institutions often face targeted attacks from nation-state actors, making it essential to understand not just the presence of malware but its purpose, command-and-control infrastructure, and evasion tactics. Hybrid analysis provides the depth and granularity needed to counter such advanced threats.
Challenges and Limitations of Hybrid Analysis
While hybrid analysis is a powerful tool, it’s not without its limitations. One major challenge is the growing sophistication of evasion techniques used by malware developers. Some malicious files are programmed to detect sandbox environments and delay execution or behave innocuously during analysis, only unleashing their payload under real-world conditions.
Dynamic analysis environments may also fail to replicate all possible execution paths. Malware might require specific user interactions, time delays, or hardware conditions that are absent in a sandbox, resulting in incomplete behavioral data. Moreover, false positives can still occur, particularly when legitimate programs exhibit behavior similar to that of malware, such as accessing system resources or encrypting files.
Resource consumption is another concern. Hybrid analysis, especially when run at scale across enterprise environments, can be computationally intensive and time-consuming. Organizations must balance the depth of analysis with performance and cost-efficiency.
Lastly, as with any security technology, hybrid analysis is most effective when integrated into a broader, layered defense strategy. It should complement, not replace, other security controls like firewalls, intrusion detection systems, and endpoint protection platforms.
Future Trends in Hybrid Analysis
The future of hybrid analysis is bright and brimming with innovation. One significant trend is the integration with real-time threat intelligence platforms, enabling instant enrichment of analysis results with context such as known malware families, actor attribution, and attack campaigns. This allows for faster, more informed decision-making.
Artificial intelligence and machine learning are also revolutionizing the field. AI can automate classification, prioritize alerts based on risk, and identify novel threats through behavioral patterns rather than static rules. As datasets grow, these systems become more accurate and capable of catching previously undetectable malware.
Cloud-based hybrid analysis is another transformative trend. It allows organizations to scale their analysis capabilities without heavy investment in hardware. Cloud services also offer API access, enabling seamless integration into CI/CD pipelines or security automation platforms.
Finally, hybrid analysis is expanding to cover emerging domains like IoT and mobile devices, which are often the weakest links in enterprise security. As more devices connect to the internet, analyzing their firmware and apps through hybrid methods will become essential for holistic cybersecurity.
Conclusion
Hybrid analysis stands at the forefront of modern malware detection and threat intelligence. By merging the static dissection of code with real-time behavioral observation, it provides a holistic, multi-layered understanding of potential threats. This dual-pronged approach makes it particularly effective against today’s evasive and complex malware variants.
As cyber threats evolve, so too must the tools used to detect and neutralize them. Hybrid analysis is not just a trend — it’s a necessity in an age where signature-based methods are no longer sufficient. Organizations that invest in this capability gain deeper visibility, faster response times, and more robust protection against both known and unknown threats.
From incident response to enterprise security, the applications of hybrid analysis are vast and growing. With advancements in AI and cloud computing, its capabilities will only expand, making it a cornerstone of future cybersecurity frameworks.
FAQs
Q1: What is the main difference between static and dynamic analysis?
Static analysis inspects code without executing it, while dynamic analysis observes the program during execution to detect malicious behavior.
Q2: Is hybrid analysis effective against zero-day threats?
Yes, hybrid analysis can detect unknown threats by analyzing code patterns and behavioral anomalies, making it effective against zero-day exploits.
Q3: Can hybrid analysis be automated in enterprise environments?
Absolutely. Many tools offer API integration, allowing automation within SIEM or SOAR platforms.
Q4: Are there any free tools for conducting hybrid analysis?
Yes, tools like Cuckoo Sandbox and the public version of CrowdStrike’s Hybrid Analysis platform are widely used in research and small-scale applications.
Q5: How does AI improve the hybrid analysis process?
AI enhances detection by learning from patterns, reducing false positives, and identifying new threats that evade traditional signatures.
You May Also Read: https://ventsworlds.com/beata-galloway/

